Dynamics 365 Tutorials, Dynamics AX Performance, Dynamics Operations Training, Microsoft Dynamics 365 Developer (F&S) Training Series, Microsoft Dynamics AX
Learn How to Implement Security Roles for Advanced User Data Protection through Dynamics AX
Security Roles for Advanced User Data Protection via D365
Security Roles | Privileges | Role Assignment | D365
Once you start using Microsoft Dynamics AX, you will know why they call this a depository for data. Business is not something to run by “trust”; your confidential information should stay as it is.
This thriving need to specified role based actions bought Microsoft to introduce security roles in Dynamics 365 Power Platform.
Today, we decided to post something quite crucial in terms of maintenance and consideration. Besides, this role based assignment has been very promising for most of our clients. So, let’s begin and see why your business needs to get started on security.
Why does your company Need role-based security?
Sooner or later, every business requires to enforce rules around how their employees are going to access or leverage the company’s information. For instance, you surely don’t want everyone having the authority to edit your customer’s data. In contrast, you want to make it visible for customer representatives to validate while on support calls.
Security configuration roles can allow your organization to perform specific operations subjected to the requestor. For example, you can use .NET to author roles-based security on principal role identity or just membership. In addition, security roles can also help you execute compliance requirements and corporate governance.
SUMMARY
In a nutshell, security policies let you define who can see what. Defining security roles frequently allows our clients to develop hierarchical charts and grant access privileges. Further, we will dive deep and get an overview of security developments in Dynamics AX, how you can assign automatic roles, exclude users from an automatic assignment, and set roles manually.
You might also want to stick till the end for some unfamiliar practices and maintenance considerations.
Understanding Security Roles in Dynamics AX
Suppose your sales team has the privilege to their lead records only, but you also want them to see some additional leads for the upcoming project. In such cases, you meet such organizational goals by using the Edit option for the roles and permission of your employees.
So, let’s begin from scratch. Anyone who wants access to Dynamics 365/AX with valid licensing requirements should be assigned to the business unit and assigned at least one security role.
This will allow the system to protect information while ensuring that users can take commensurate actions according to their roles.
Security Roles are forged with privileges and access levels defined for each role.
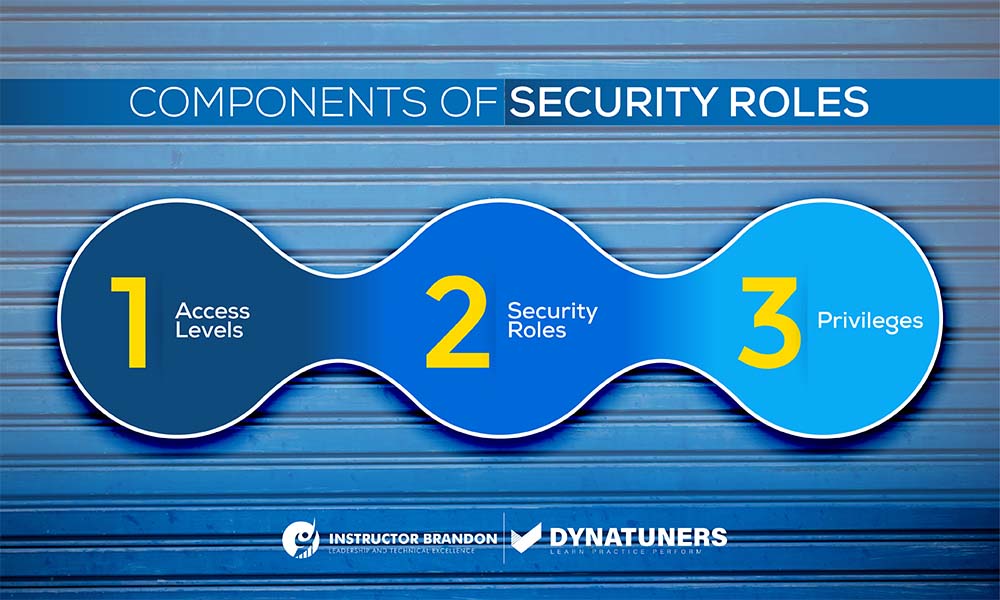
Privileges
Privileges are the lowest security level in the Dynamics AX Security Module. Primarily, it consists of CRUDE level permissions that you can tweak to make any granular security requirement. Privileges consist of access to:
- Create
- Read
- Update
- Delete
- Edit
You can also add security privileges directly to the security administrator to meet certain requirements, and it is the best way to assign it to a duty. Take them as a gateway for gaining access to any secure object in the workspace.
The table will help understand privileges for the level of access controls more briefly.

The privileges mentioned above are known as record-level privileges. They define what actions a user can perform. However, some privileges are not directly linked to any entity but allows a person to perform certain tasks. These tasks include access to read published e-mails, export data to excel, access to edit in bulk quantities, view audit history, etc. They are called task-based privileges.
Access Controls determine the user’s scope of the data. The below table defines access controls.
| User Access Levels or Keys | |
| No Access | The system will grant no privileges by default unless you assign the user a role. |
| Basic | Users have the privilege to share data owned by other users or teams. |
| Local | With the local key, the user gets privileges to all records on parent role in the business belonging to any user. |
| Deep | Users with this access level have access to records in their own business units and all business units that are a subset of their own. Users who have Deep access also have Basic and Local access. |
| Global | Users with this access level have access to all records, regardless of their business unit or job description. Other accesses, such as deep, local, and basic are automatically granted to users with Global access. Because global access is so powerful, it must be granted carefully. It should ideally only be given to managers and other high-ranking officials. |
The hierarchical table below will further help you understand access controls.
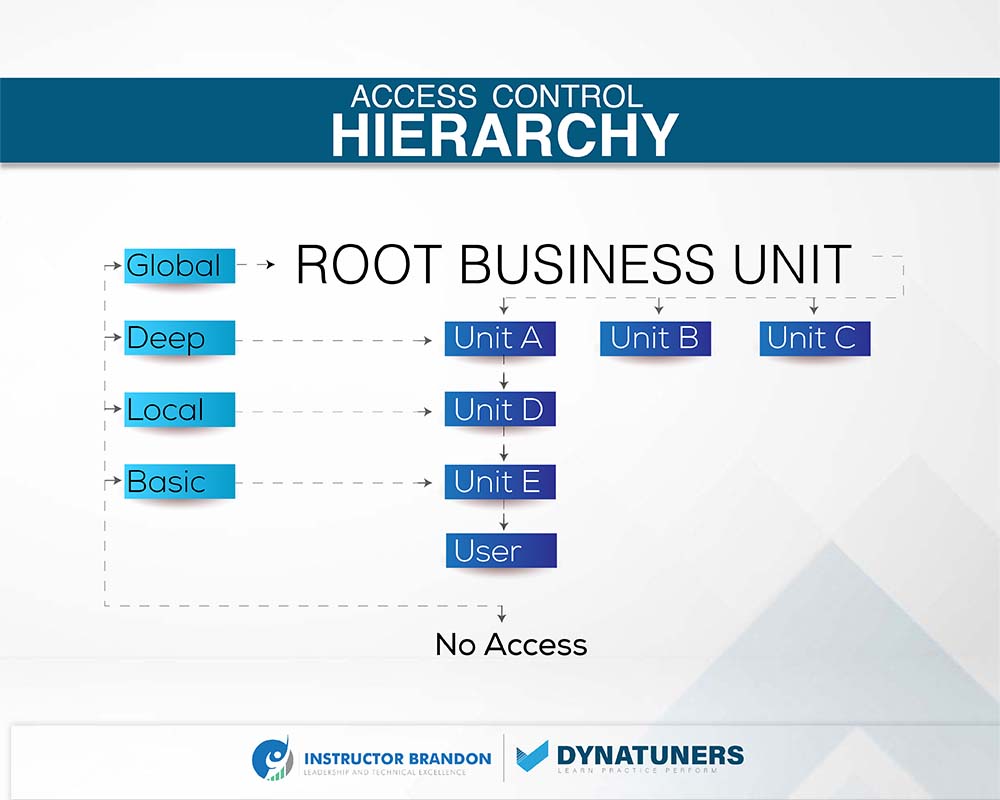
SUMMARY
Security is a critical part of ERP deployments that is often disregarded, resulting in problems later in the project. Implementing security practices, assigning and testing security roles is critical to a successful implementation.
The security system in Dynamics AX is extremely flexible, and once you get familiar with it, it’s really simple to utilize. We hope that the above tables and charts have demonstrated some of the security management fundamentals and security jobs. Now let’s move on to how you can assign security roles in Dynamics 365 FO/AX.
Automatically assign users to roles
Step 1
Go to Navigation pane > Modules > System administration > Security > Assign users to roles.
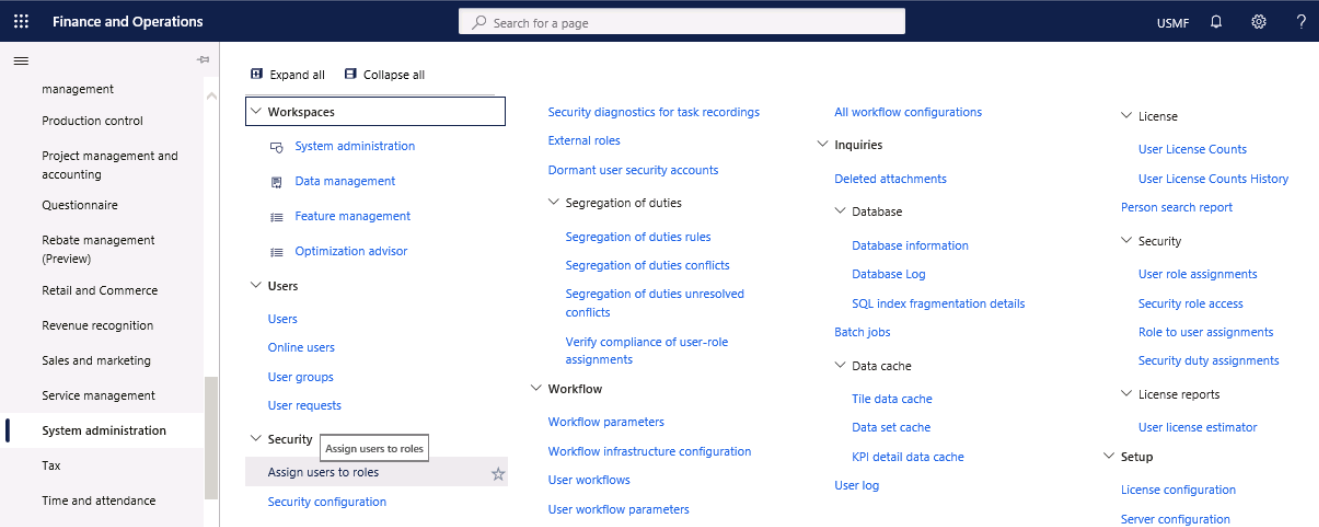
Step 2
In the tree, select ‘Accounting supervisor.’ Next, select the role that you want to configure the rule for. In this example, select Accounting Supervisor.
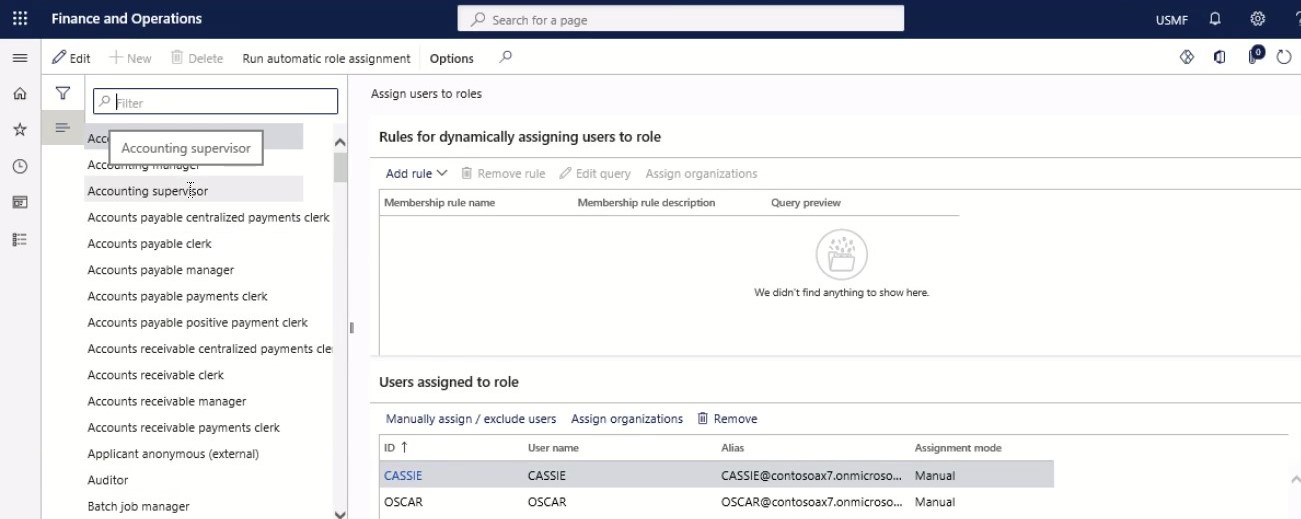
Step 3
Select Add Rule to open the dialogue menu.
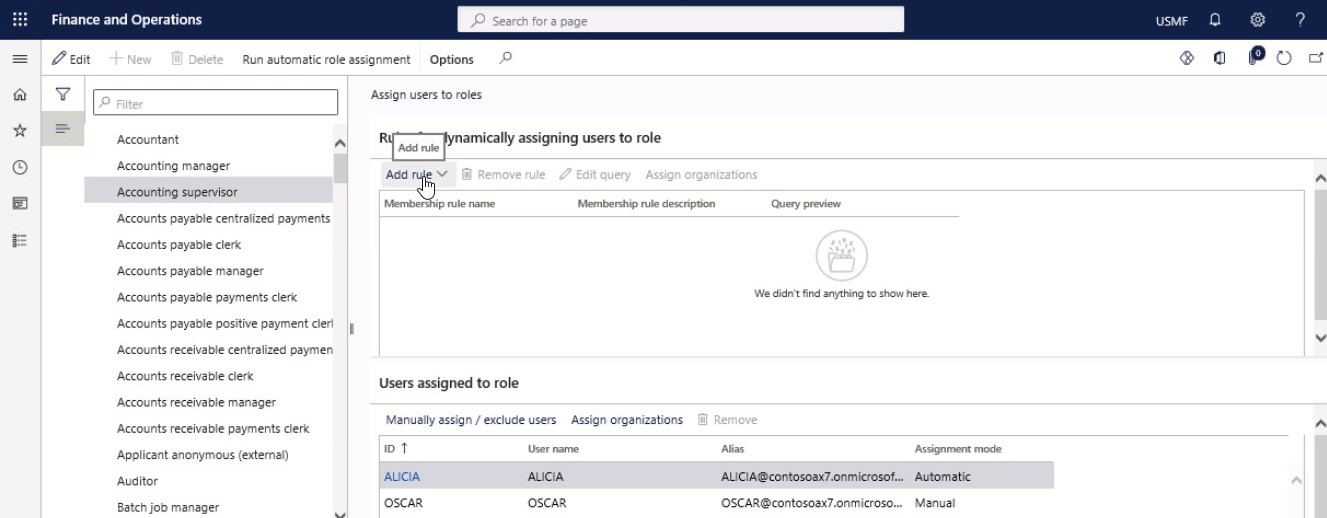
Step 4
Select a query list, find and select the desired record. Then, select the query to use for this rule.
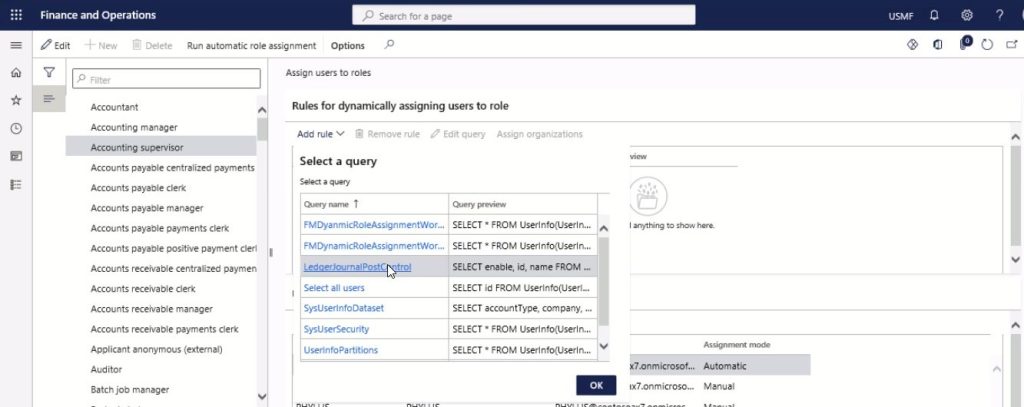
Step 5
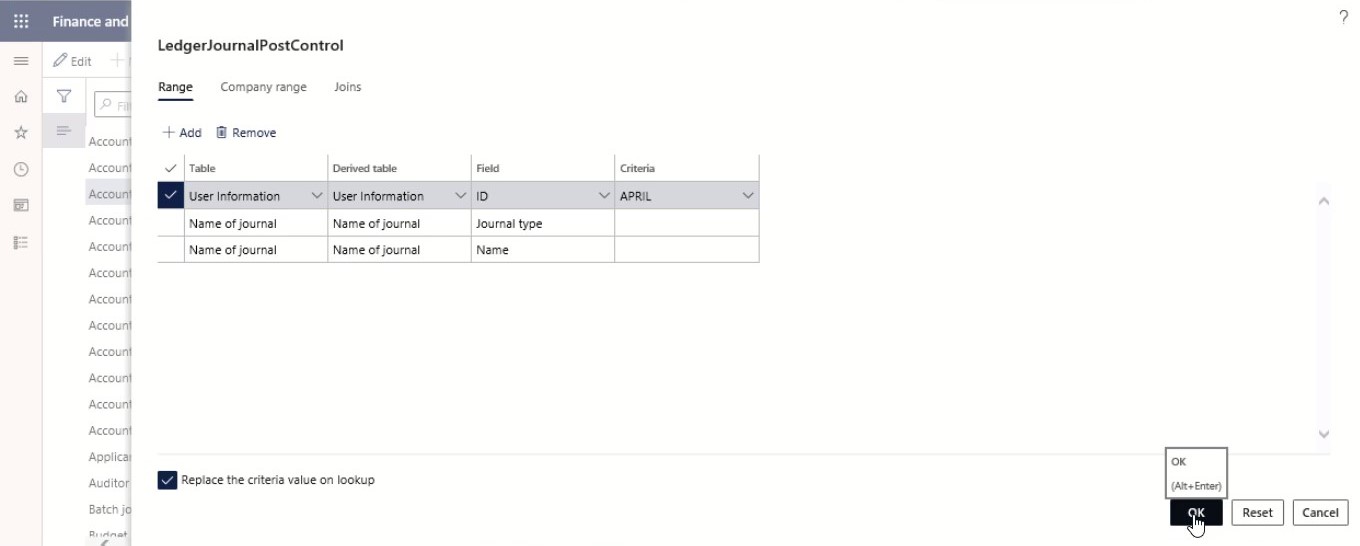
Select Edit query. Edit the query as needed.
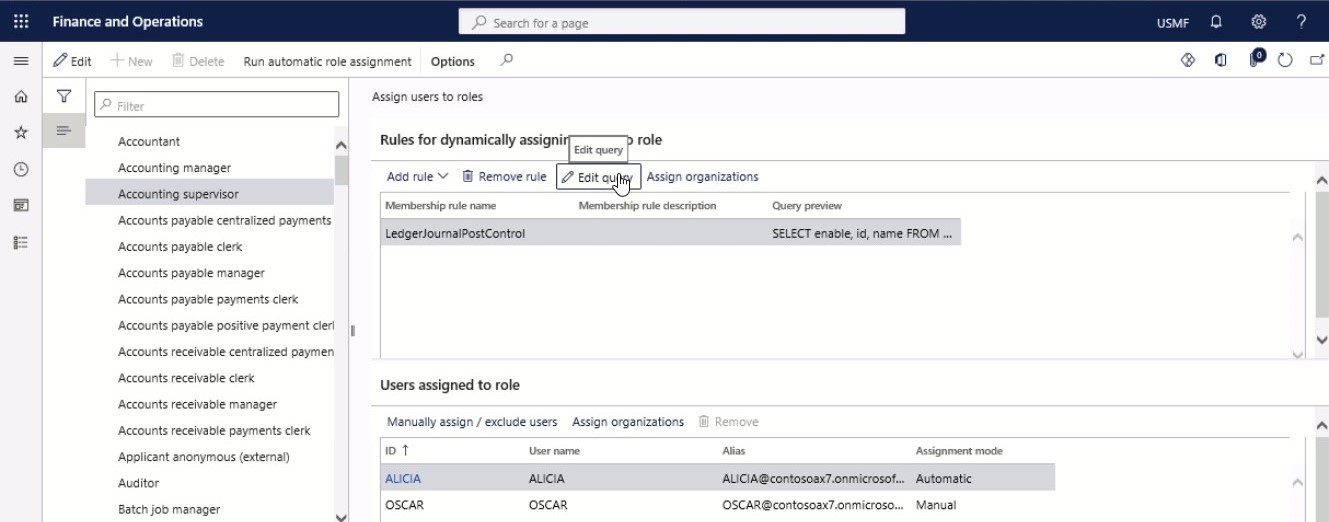
Step 6
Select OK.
Step 7
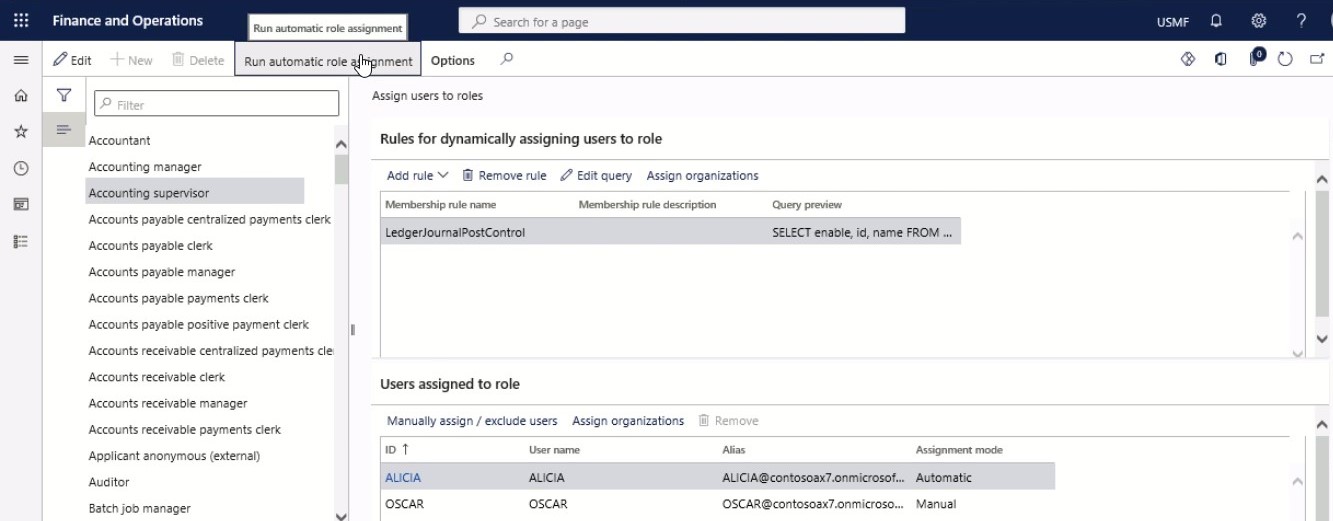
Select Run automatic role assignment.
Step 8
Go to Navigation pane > Modules > System administration > Users > Users (ideally in a separate browser tab).
Step 9
Review the roles assigned to various users to confirm that the role assignment query was correct. Adjust and re-run if needed.
Exclude users from automatic role assignment
Step 1
Close the page.
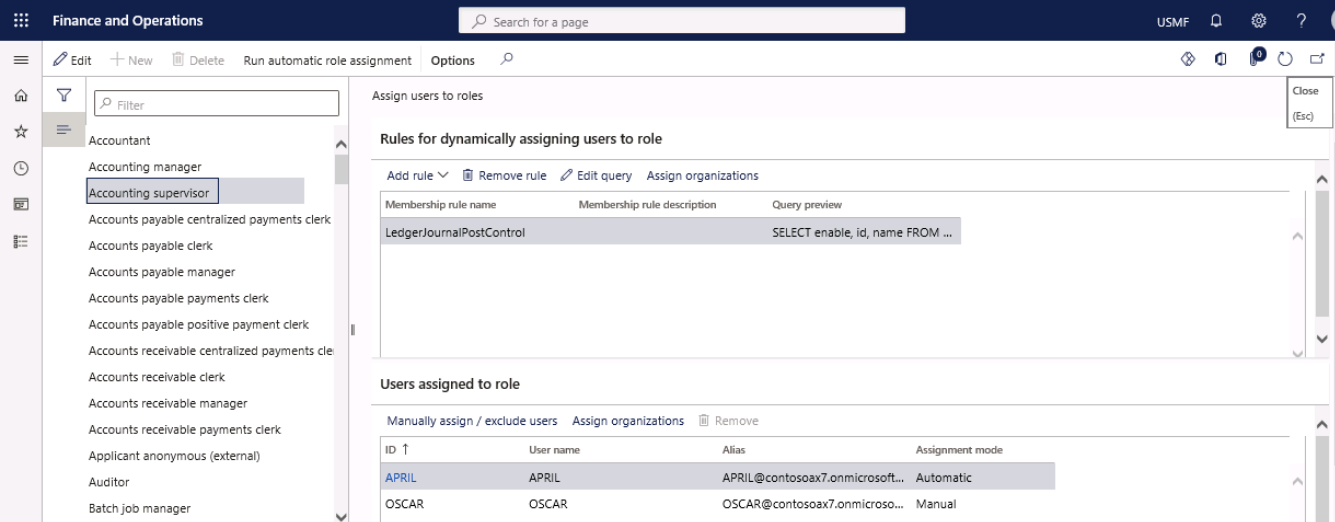
Step 2
Go to Navigation pane > Modules > System administration > Security > Assign users to roles.
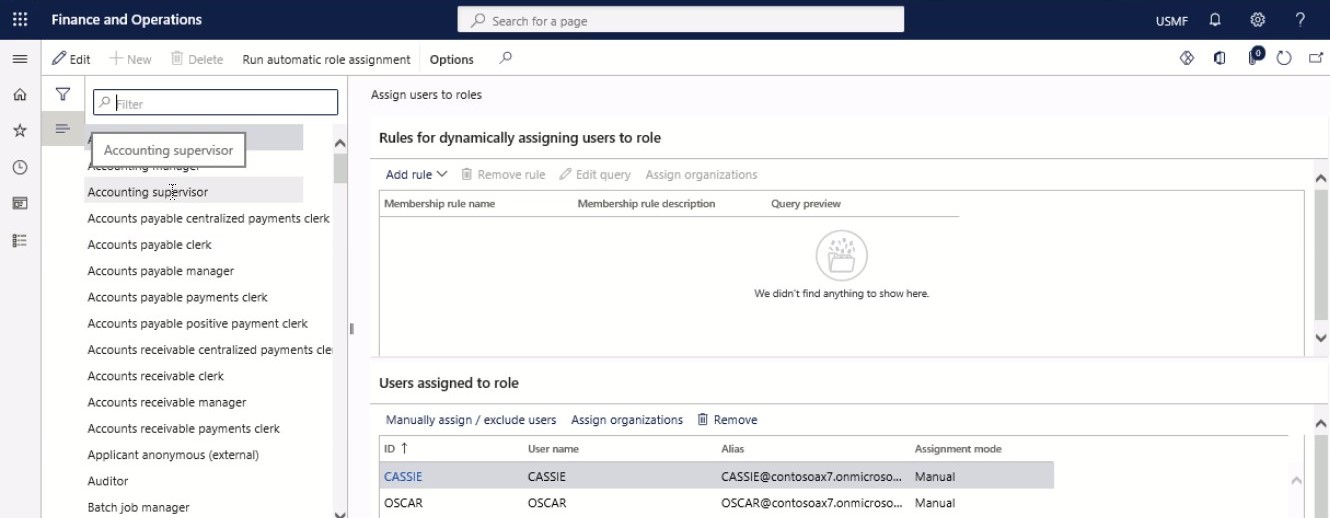
Step 3
In the tree, select ‘Accounting supervisor.’ Select a role. For this example, select an accounting supervisor.
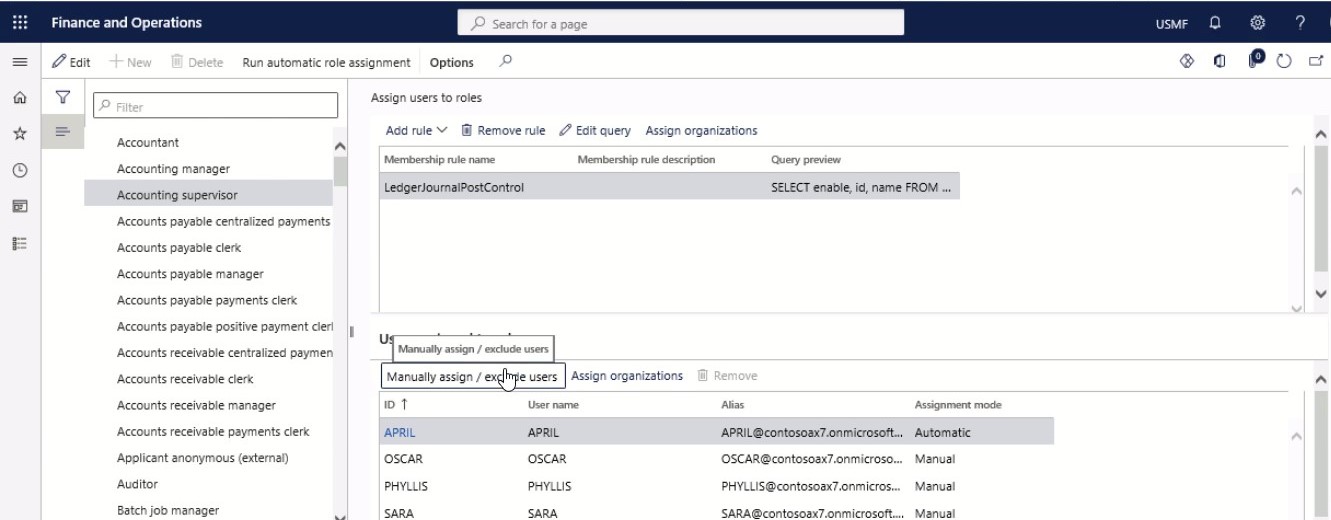
Step 4
In the Users assigned to role menu, select Manually assign/exclude users.
Step 5
In the Assign users to or exclude users from role list, mark the selected row. Select a user.
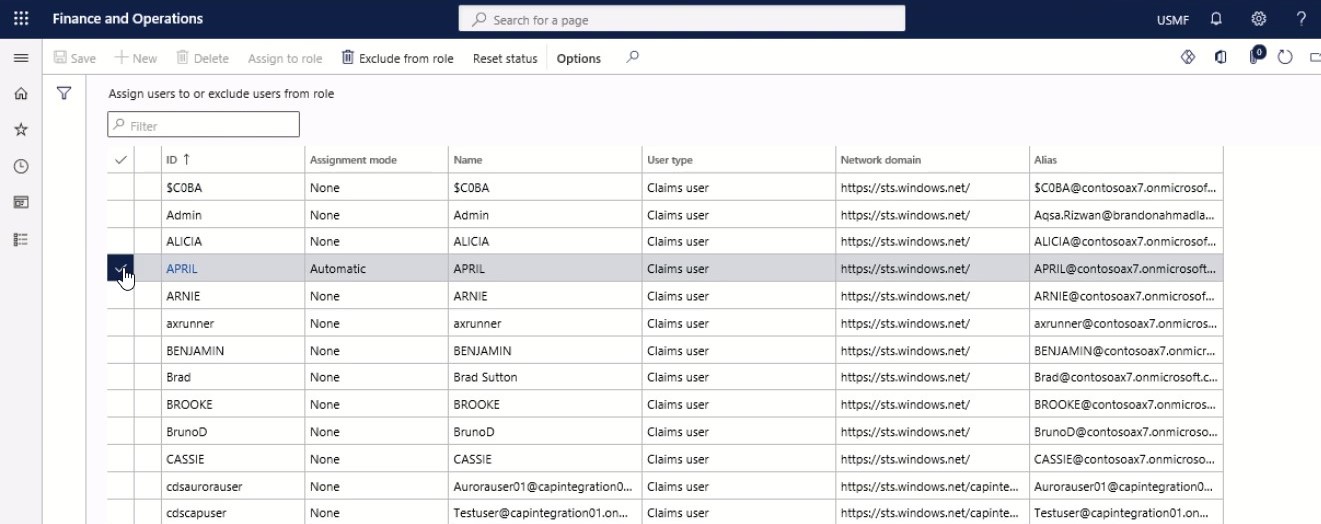
Step 6
On the Action pane, select Exclude from the role.
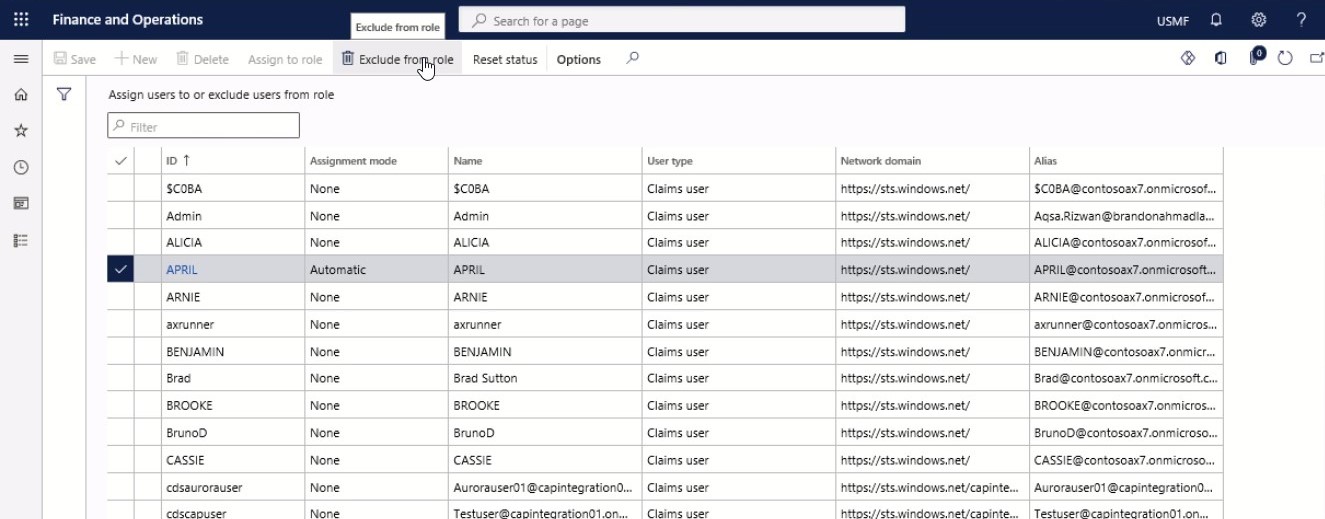
Step 7
Select Exclude from role to exclude the selected users from the role. To remove exclusions, select the users that you want to remove exclusions for, and then click Reset status.
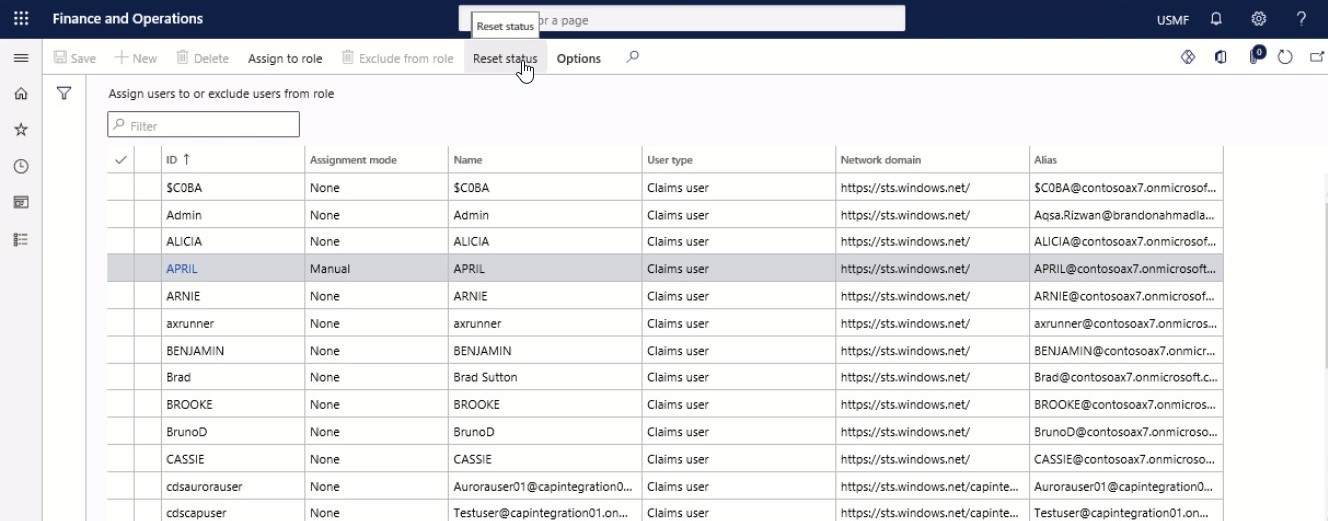
Note: When you remove an exclusion by resetting the user’s status, the user’s role is assigned automatically. However, the user is not instantly assigned to the role or excluded from the role. Instead, the changes are applied when the next time role assignment rules are run.
Manually assign users to roles
Users who are manually assigned to security roles must also be manually removed by the system administration.
Step 1
Go to Navigation pane > Modules > System administration > Security > Assign users to roles.
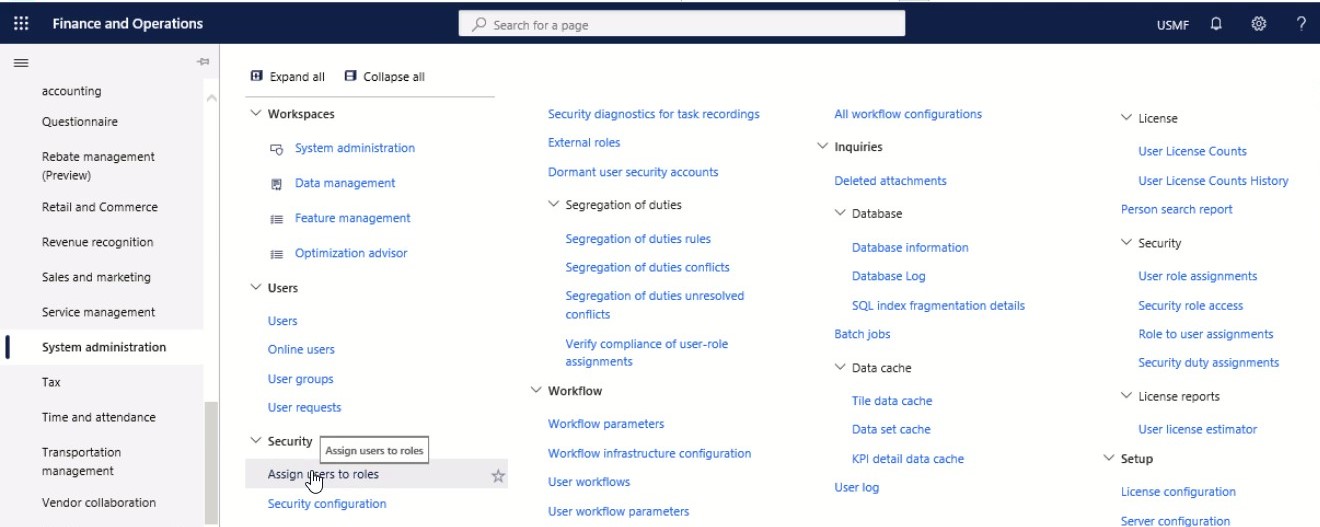
Step 2
In the tree, select a role, and in the Users assigned to role menu, select Manually assign/exclude users.
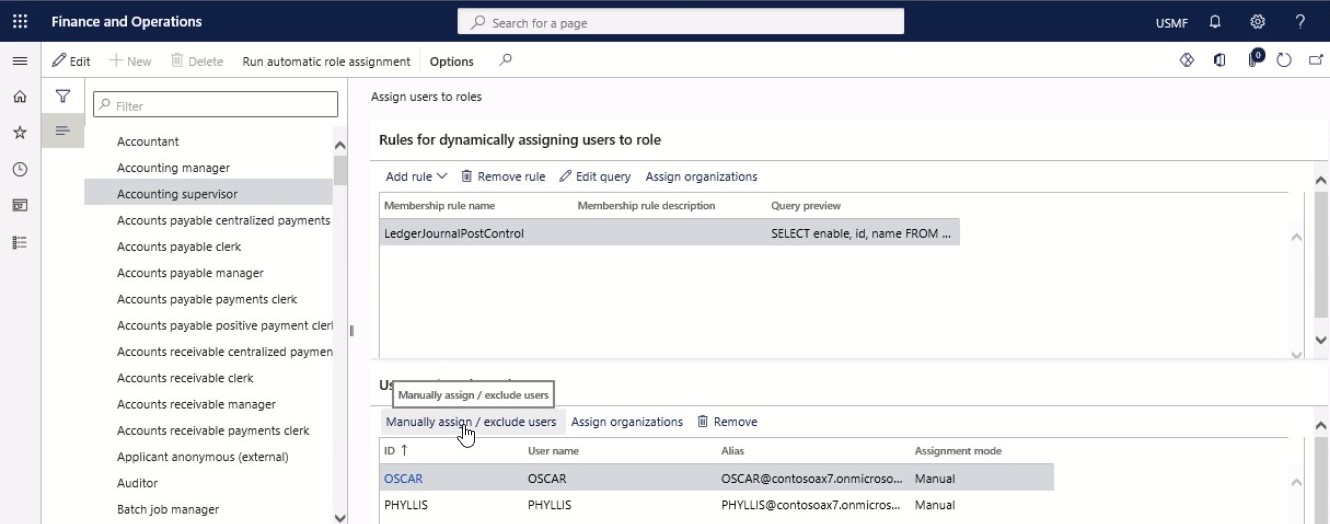
Step 3
In the Assign users to or exclude users from role, users that have not been assigned the role are listed with the Assignment mode set to None. Select one or more users that should be assigned the role.
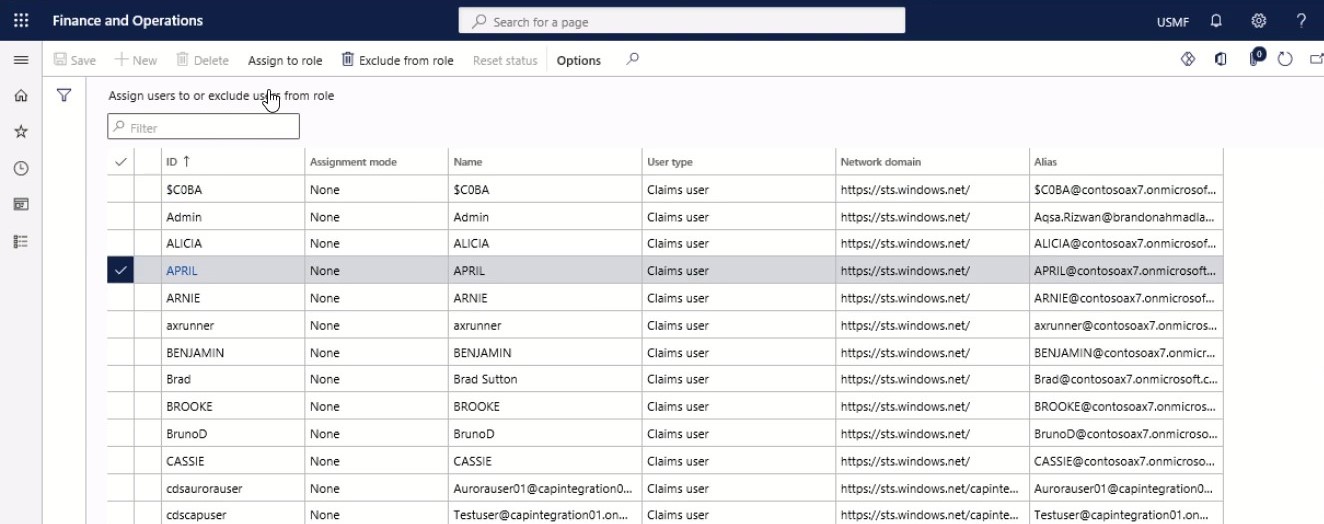
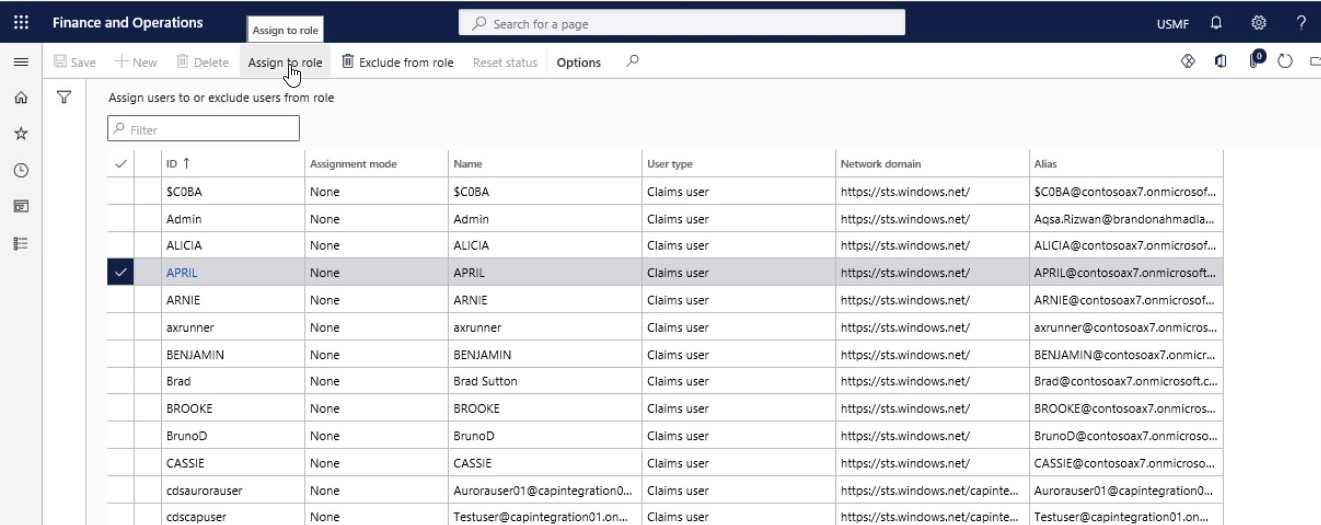
Step 4
On the Action pane, select Assign to role. The Assignment mode is updated to Manual and the users now have a new role assigned.
SUMMARY
While assigning a security role to a user, you must first have the necessary privileges. Read and Assign are the only privileges you’ll need. To prevent misuse of privileges, you can’t give the assignee a security job with more privileges than yours. As a result, if you’re a CSR Manager, you can’t give another user the System Administrator role.
By default, the System Administrator has all of the necessary privileges, including assigning security roles to any user, including the System Administrator job. This is the highest position with the capacity to grant and deny access and determine the scope of rights.
Things You Should Look out for Security Maintenance
Due to the strict regulations of GDPR and rising cybercrime activities, security management has become a crucial aspect of businesses.
When it comes to your business data security, your administrator is required to go above and beyond and look out for the following things while considering your security upgrades.
Do not use CRM’s Business Units as the ultimate organizational structure
Contrary to popular belief, your organizational structure rarely matches one-to-one with the business processes ideal for your organization. That means, in a large organization, different departments require collaboration every now and then.
That is why, using CRM business unit as your ultimate organizational structure could place limitations on their collaboration and restrict them while performing certain tasks.
Teams are more adaptable than Business Units
“Business Units” are a great way to maintain data security between divisions inside your company. However, employ caution when using Business Units, which requires a less adaptable security model.
Is it common for a team member from one department to temporarily work with colleagues from another department? Then you should group your users into “Teams”. “Teams” allow you to add a CRM user as a team member temporarily. Each user who is a member of the Team instantly inherits the Team’s user rights. When the helpful colleague’s temporary involvement is over, you can remove them from the Team once again.
Business Units should be viewed as a technique to divide your CRM database into logical sections.
If you want to keep data regarding sales opportunities segregated, business units are essential for managing data amongst employees who are not working on the same data.
Use caution when revoking permissions
It is a generally acceptable premise that CRM users should not erase data because they might want to run reports in CRM on all information. The main issue with Delete permissions is that records might be deleted inadvertently. In that circumstance, a “disaster recovery” is required, that is both complex and time-consuming.
“Deactivate” is an alternative to “Delete”. Because deactivated records are not displayed in the lists, this ensures that you are no longer confronted with the deactivated record. However, if necessary, you can still seek up this record, as it hasn’t completely vanished.
SUMMARY
Managing security across Microsoft Dynamics 365 modules and other service operations can be complex. However, by incorporating some of these best security practices and maintenance advice into your overall security approach, your administrators and end-users can benefit from it.
Closure
Aren’t security roles exciting? They ensure that your company and data are completely secure and that unauthorized users do not have access to information they shouldn’t have. Although all this appears easy-to-go; however, it is okay to feel overwhelmed with all the features out there.
Do you think your company requires security enhancements? If so, we can assist you with all of Dynamics AX fundamentals and its sophisticated functionalities. Proper training will not only keep your team from hitting any snags but will also ensure that they get to appreciate all of the platform’s fantastic features.
If you have any queries regarding security settings in Dynamics 365 FO/AX, feel free to get in touch.
At Instructor Brandon | Dynatuners, we always seek innovative methods to improve your competitiveness and suit your Microsoft Dynamics 365 requirements. Our offerings are founded on defined procedures, industry experience, and product understanding. If you’re interested in consulting with our specialists on how it may benefit you to implement security based roles and access level privileges to enhance security aspect for your company, don’t hesitate to Contact Us.
Who can assign security roles in Dynamics 365?
A set of security roles is included by default in Dynamics 365 Sales Professional: Professional salesperson, manager of Sales Professionals, and the administrator of the system
What are security roles?
A security role is a set of project-level privileges assigned to individuals and groups. In a project, a security role is a set of privileges. On a project-by-project basis, those privileges are assigned as a set to various users or groups.
How do I test security roles in Dynamics 365?
The simplest solution is to create a new Azure Active Directory user account Testuser@mycompany.com. Then, add this user in your system and assign your user role to them. Then, as Testuser@mycompany.com, log in to the system.

 3033
3033