Tag Archives: Sevice Fabric
OnPremise Tutorials Part 4: Simple way to get modern Certificates and Security Correct for your Service Fabric, AX 7 (Dynamics Operations) installation
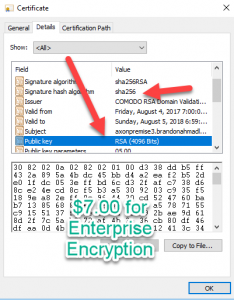
Contrary to popular mythology, we don’t have to use outdated legacy, fully exploitable sha1 security [...]
07
Aug
Aug